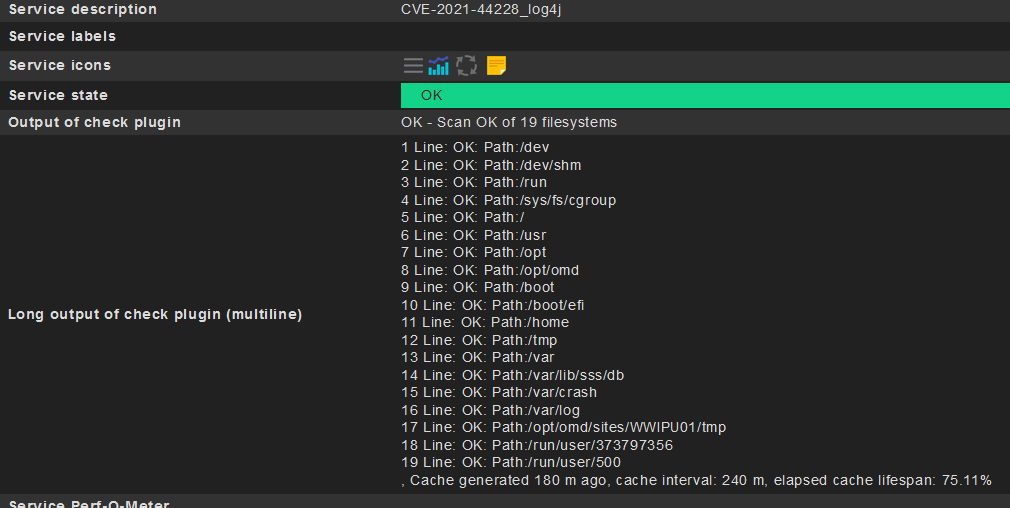
Hello all
I’ve written a script for Linux to get better informationn about the log4j problem by using the provided scan tool.
But my problem is the Windows PowerShell script to write.
Is somebody able to translate my Shell script in to PowerShell script?
#!/bin/bash
# ================================================================================================================================
#
# Author: Jan-Philipp Henkel
# Local Identifier: W&W Informatik
# Filename: wwi_log4j_scan.sh
# Description: log4j security serach
# Version: 1.0
# Requester: xxxx
# Requirements:
#
#
# Changes:
# Date: Author: Changes:
# 17.12.2021 JPH initial Version
#
# =================================================================================================================================
#
#
# Christian Wirtz, 2021-12-15
# Wrapper around:
# https://github.com/logpresso/CVE-2021-44228-Scanner
# for checkmk usage - used Logpresso CVE-2021-44228 Vulnerability Scanner 1.6.2
# https://github.com/logpresso/CVE-2021-44228-Scanner/releases/download/v1.6.2/logpresso-log4j2-scan-1.6.2-linux.tar.gz
# extract this into ../../bin/
#
# Forum:
# -------------------------
# https://forum.checkmk.com/t/checkmk-not-affected-by-log4shell/28643/2
#
# Info and files
# -------------------------
# https://github.com/logpresso/CVE-2021-44228-Scanner
# Linux
# https://github.com/logpresso/CVE-2021-44228-Scanner/releases/download/v2.0.0/logpresso-log4j2-scan-2.0.0-linux.tar.gz
# AIX
# https://github.com/logpresso/CVE-2021-44228-Scanner/releases/download/v2.0.0/logpresso-log4j2-scan-2.0.0.jar
#
#
# example output
# ------------------
#./log4j2-scan /usr/
#Logpresso CVE-2021-44228 Vulnerability Scanner 2.0.0 (2021-12-17)
#Scanning directory: /usr
#
#Scanned 8671 directories and 72096 files
#Found 0 vulnerable files
#Found 0 potentially vulnerable files
#Found 0 mitigated files
#Completed in 0.55 seconds
#
# variables
# ------------------
# Info:
# -------------------------
# Text Marker:
# ( ) = OK
# (?) = UNKNOWN
# (!!) = CRITICAL
# (!) = WARNING
#
#
# possible return values
# --------------------------
STATE_OK=0
STATE_WARNING=1
STATE_CRITICAL=2
STATE_UNKNOWN=3
# Log Date
# -------------------------
LOG_DATE=$(date +%Y_%m_%d"-"%H_%M_%S)
# DATE_PRINT=$(date +%H:%M:%S" "%d.%m.%Y)
SCRIPT_NAME=$(echo $0|awk -v FS="/" '{print $NF}'|awk -v FS="." '{print $1}')
TEXT_INFO="UNKNOWN OPTION: usage: $0 [-c Critical_Error_Count] [-w Warning_Error_Count] \n -c 3 -w 2 -p /usr/"
#for PATH in $(/usr/bin/df -l|grep -v "Filesystem"|/usr/bin/awk '{print $NF}'|/usr/bin/grep -v "^/$"); do
for PATH in $(/usr/bin/df -l|grep -v "Filesystem"|/usr/bin/awk '{print $NF}'); do
# |/usr/bin/head -1
COUNTER_PATH=$((COUNTER_PATH + 1))
# checking the option
# ---------------------------
#PATH="/"$(echo $SCRIPT_NAME|/usr/bin/awk -v FS="_" '{print $4}')"/"
CHECKER="OK"
ERROR_COUNTER=0
COUNTER=0
COUNTER_CHECK=0
ERROR_LINES=""
while read LINE || [ -n "$LINE" ]; do
COUNTER=$((COUNTER + 1))
if ( echo $LINE|/usr/bin/grep -q "Found " ); then
COUNTER_CHECK=$((COUNTER_CHECK + 1))
if ( echo $LINE|/usr/bin/grep "Found"|/usr/bin/grep -q "0" ); then
ARRAY_LINES[$COUNTER]="Line ${COUNTER}:${LINE}|"
else
ERROR_LINES="${ERROR_LINES};${LINE}(!!)"
ARRAY_LINES[$COUNTER]="Line ${COUNTER}:${LINE}(!!)|"
CHECKER="CRITICAL"
ERROR_COUNTER=$((ERROR_COUNTER + 1))
fi
else
ARRAY_LINES[$COUNTER]="Line ${COUNTER}:${LINE}|"
fi
#done < <(/usr/lib/check_mk_agent/log4j2-scan $PATH|/usr/bin/sed '/^$/d'|/usr/bin/sed 's/Found 0 /Found 2 /g')
done < <(/usr/lib/check_mk_agent/bin/log4j2-scan $PATH|/usr/bin/sed '/^$/d')
CHECK_LINES=$(echo ${ARRAY_LINES[*]}|/usr/bin/tr '|' '\n'|/usr/bin/grep "Found "|/usr/bin/tr '\n' ';')
SERVICE_NAME="CVE-2021-44228_log4j_path_$PATH"
LONG=`echo "${ARRAY_LINES[*]}"|/usr/bin/sed 's/|/\\\n/g'`
ARRAY_PATH_OK_CHECK[$COUNTER_PATH]="$COUNTER_PATH Line: OK: Path:$PATH |"
ARRAY_PATH_CRITICAL_CHECK[$COUNTER_PATH]="$COUNTER_PATH Line: CRITICAL: Path:$PATH (!!) $ERROR_LINES|"
ARRAY_CHECKER[$COUNTER_PATH]="${CHECKER}:$PATH|"
done
if ( echo ${ARRAY_CHECKER[*]}|/usr/bin/grep -q "CRITICAL:" ); then
#echo "2 CVE-2021-44228_log4j Scan CRITICAL: ${ARRAY_CHECKER[*]}\n$(echo ${ARRAY_PATH_CRITICAL_CHECK[*]}|/usr/bin/sed 's/|/\\\\\n/g')"
echo "2 CVE-2021-44228_log4j - Scan CRITICAL: ${ARRAY_CHECKER[*]} \n $(echo ${ARRAY_PATH_CRITICAL_CHECK[*]}|/usr/bin/sed 's/|/\\\\\n/g')"
else
#echo "0 CVE-2021-44228_log4j Scan OK\n$(echo ${ARRAY_PATH_OK_CHECK[*]}|/usr/bin/sed 's/|/\\\\\n/g')"
echo "0 CVE-2021-44228_log4j - Scan OK of $COUNTER_PATH filesystems \n $(echo ${ARRAY_PATH_OK_CHECK[*]}|/usr/bin/sed 's/|/\\n/g')"
fi
exit
if [ "$CHECKER" != "OK" ]; then
echo "2 $SERVICE_NAME Scan CRITICAL: state of $COUNTER_CHECK checks CRIT-Count:${ERROR_COUNTER}(!!) $ERROR_LINES \n$LONG"
else
echo "0 $SERVICE_NAME Scan OK: state of $COUNTER_CHECK checks $CHECK_LINES \n$LONG"
fi
exit $STATE_UNKNOWN
wwi_log4j_scan.sh (5 KB)
reason the provided scripts don’t show any details which we need.
This would be perfect.
Thanks
Best regards
Jan-Philipp