yes check as reciever or use a central syslog system to collect and manage als systems.
For example a ELK Stack or first tests splunk free 500MB per day.
Ralf
If you have the data on the CMK server.
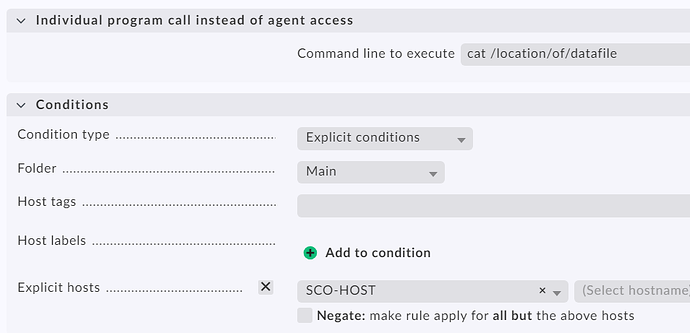
You can create a “Individual program call instead of agent access” rule

like this
this file must be readable by the CMK site user.
The setting for the SCO host should look like this.
Now you can do a discovery - if the data inside the file correspond to normal agent data something should be found.
Thank you that looks very promising.
The file should have the format?:
<<<key1>>>
value1
<<<key2>>>
value2
Going to try that tomorrow
Attention this is not a key like in key value pairs. This is the name of an agent section.
This must correspond to a check plugin inside CheckMK.
What you named as value is the raw output that will be processed by the named agent plugin.
I did the command to execute with a script and made a few python plugins in …/cmk/base/plugins/agent_based to catch the data.
Works just fine.
My zabbix knowledge was somewhat of a setback. CMK is very different.
Thank you very much! Im very happy.
The only common thing between Zabbix and CheckMK is i think that it is booth times Python ![]()
But this week i used a Zabbix plugin to write a CheckMK special agent. And this was a relativ easy conversion if you know the CheckMK plugin system. Without this it is way harder.
This topic was automatically closed 365 days after the last reply. New replies are no longer allowed. Contact an admin if you think this should be re-opened.