Dear Check_MK Community,
I’m trying to deploy alerthandlers to restart systemd-services if they’re down (works well on my test server with Ubuntu 20.04 and root-login allowed).
Now I’m faced with the situation that root login via SSH is not permitted on the target host.
Check_MK Enterprise Edition 1.6.0.p15 (will be upgraded shortly to 1.6.0p17).
I have the following Rules:
(not showing the Systemd Service rules because they work and have been tested)
Remote alert handlers (Linux)
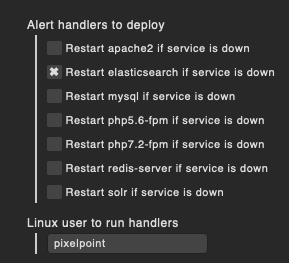
Alerthandler configuration
For this to work though, I needed to set permissions on different
Now I have a big question mark above my head:
Why do i need to set 2 Users in 2 different places?
How do others deploy alerthandlers without root access?
Do you really need to manually change permissions to different files on all your target hosts just to get this running without root access?
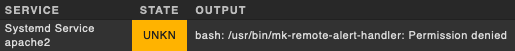
alert.log (on checkmk server) output
Rule 'restart if service is down after 2nd check attempt (apache2)'...
Event Type is rc
-> matches!
Executing alert handler linux_remote for HOSTNAMEREDACTED;Systemd Service apache2
Spawned event handler with PID 25924
Handler [25924] linux_remote HOSTNAMEREDACTED;Systemd Service apache2 stopped: bash: /usr/bin/mk-remote-alert-handler: Permission denied
alert handler execution view
permissions on /usr/bin/mk-remote-alert-handler on target server
P.S.:
Yes, the screenshots say elasticsearch (i made a screenshot of the wrong rule at first), but as you see we also want to restart apache2 via alerthandler.
Also: Just for testing, I got rid of the “only start alerthandlers on 2nd check attempt” portion of the rule.
Everything else is the same and I will definitely bring that portion back once the alerthandlers work.
If you need any more information, pls tell me.
I’m looking forward to your answers.
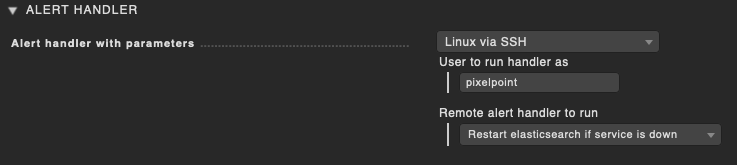
 ), you should try to limit the access as far as possible.
), you should try to limit the access as far as possible.