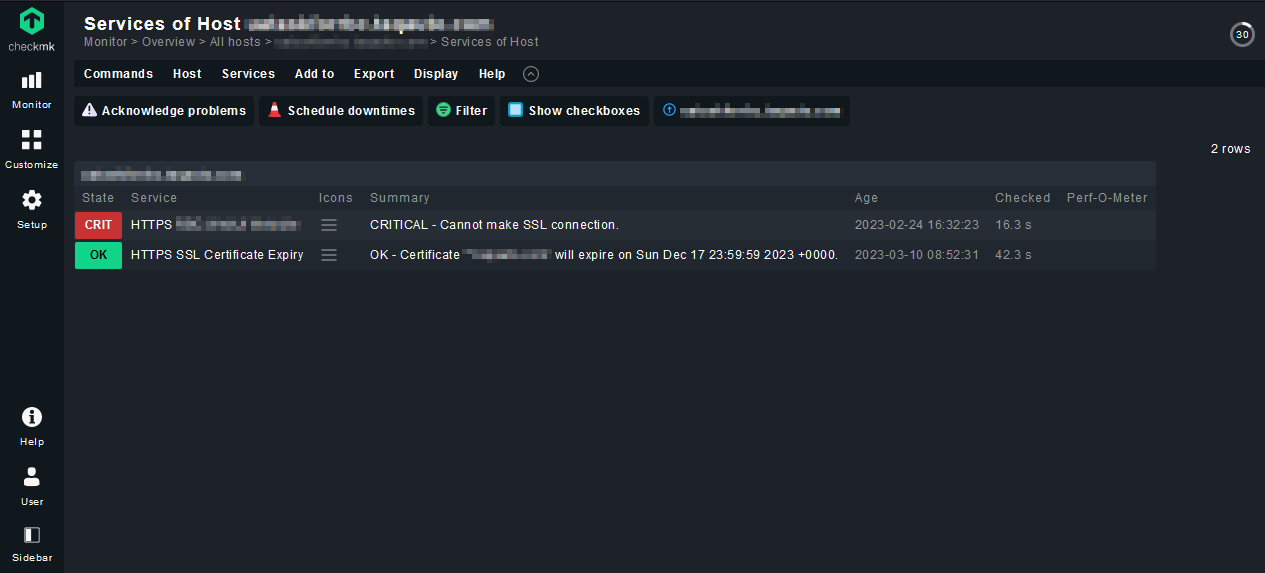
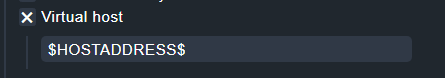
Thank you for the suggestion Anders.
I tested using cURL from the site’s command line and confirmed that the connection is established as expected. I also tested another instance of the site (that is working in Checkmk) for comparison but both seem to be the same.
OMD[site]:~$ curl -vv https://uathostname.domain.com/healthcheck/healthcheck.html
* Trying 1.2.3.4:443...
* TCP_NODELAY set
* Connected to uathostname.domain.com (1.2.3.4) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /omd/sites/cama/var/ssl/ca-certificates.crt
CApath: /etc/ssl/certs
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (IN), TLS handshake, CERT verify (15):
* TLSv1.3 (IN), TLS handshake, Finished (20):
* TLSv1.3 (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: CN=*.domain.com
* start date: Nov 16 00:00:00 2022 GMT
* expire date: Dec 17 23:59:59 2023 GMT
* subjectAltName: host "uathostname.domain.com" matched cert's "*.domain.com"
* issuer: C=GB; ST=Greater Manchester; L=Salford; O=Sectigo Limited; CN=Sectigo RSA Domain Validation Secure Server CA
* SSL certificate verify ok.
> GET /healthcheck/healthcheck.html HTTP/1.1
> Host: uathostname.domain.com
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Content-Type: text/html
< Last-Modified: Fri, 03 Mar 2023 17:07:58 GMT
< Accept-Ranges: bytes
< ETag: "0abe9b3f24dd91:0"
< Server: Microsoft-IIS/8.5
< X-Powered-By: ASP.NET
< X-Frame-Options: SAMEORIGIN
< Date: Fri, 17 Mar 2023 15:37:00 GMT
< Content-Length: 3
< Strict-Transport-Security: max-age=0
<
* Connection #0 to host uathostname.domain.com left intact
OMD[site]:~$ curl -vv https://hostname.domain.com/healthcheck/healthcheck.html
* Trying 146.20.205.156:443...
* TCP_NODELAY set
* Connected to hostname.domain.com (146.20.205.156) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /omd/sites/cama/var/ssl/ca-certificates.crt
CApath: /etc/ssl/certs
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (IN), TLS handshake, CERT verify (15):
* TLSv1.3 (IN), TLS handshake, Finished (20):
* TLSv1.3 (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384
* ALPN, server accepted to use http/1.1
* Server certificate:
* subject: REDACTED
* start date: Jan 31 00:00:00 2023 GMT
* expire date: Mar 2 23:59:59 2024 GMT
* subjectAltName: host "hostname.domain.com" matched cert's "hostname.domain.com"
* issuer: C=US; O=DigiCert Inc; CN=DigiCert Global G2 TLS RSA SHA256 2020 CA1
* SSL certificate verify ok.
> GET /healthcheck/healthcheck.html HTTP/1.1
> Host: hostname.domain.com
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Content-Type: text/html
< Last-Modified: Thu, 16 Dec 2021 02:33:14 GMT
< Accept-Ranges: bytes
< ETag: "0516d4625f2d71:0"
< Server: Microsoft-IIS/8.5
< X-Powered-By: ASP.NET
< X-Frame-Options: SAMEORIGIN
< Date: Fri, 17 Mar 2023 15:37:14 GMT
< Content-Length: 3
< Strict-Transport-Security: max-age=157680000
<
* Connection #0 to host hostname.domain.com left intact
OMD[site]:~$
Any other thoughts on possible troubleshooting steps?
Regards,
Jason