CMK version:
2.0.0p23
OS version:
RHEL7
Error message:
Updated the certificate store "/var/lib/check_mk_agent/cas/all_certs.pem" with 1 certificate(s)
Going to register agent at deployment server
Trying to import certificate from the server's certificate chain but found no self-signed certificate or CA certificate. Aborting import.
HTTPSConnectionPool(host='mymonitoringserver.it', port=8443): Max retries exceeded with url: /cmk/check_mk/login.py (Caused by SSLError(SSLError("bad handshake: Error([('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')])")))
See syslog or Logfile at /var/lib/check_mk_agent/cmk-update-agent.log for details.
“/var/lib/check_mk_agent/cmk-update-agent.log”:
2023-09-15 10:51:40,698 DEBUG: Authenticating at Checkmk Server (using requests): https://mymonitoringserver.it:8443/cmk/check_mk/login.py
2023-09-15 10:51:40,705 DEBUG: Caught Exception:
Traceback (most recent call last):
File "site-packages/urllib3/contrib/pyopenssl.py", line 488, in wrap_socket
File "site-packages/OpenSSL/SSL.py", line 1934, in do_handshake
File "site-packages/OpenSSL/SSL.py", line 1671, in _raise_ssl_error
File "site-packages/OpenSSL/_util.py", line 54, in exception_from_error_queue
OpenSSL.SSL.Error: [('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')]
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "site-packages/urllib3/connectionpool.py", line 677, in urlopen
File "site-packages/urllib3/connectionpool.py", line 381, in _make_request
File "site-packages/urllib3/connectionpool.py", line 976, in _validate_conn
File "site-packages/urllib3/connection.py", line 370, in connect
File "site-packages/urllib3/util/ssl_.py", line 377, in ssl_wrap_socket
File "site-packages/urllib3/contrib/pyopenssl.py", line 494, in wrap_socket
ssl.SSLError: ("bad handshake: Error([('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')])",)
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "site-packages/requests/adapters.py", line 449, in send
File "site-packages/urllib3/connectionpool.py", line 725, in urlopen
File "site-packages/urllib3/util/retry.py", line 439, in increment
urllib3.exceptions.MaxRetryError: HTTPSConnectionPool(host='mymonitoringserver.it', port=8443): Max retries exceeded with url: /cmk/check_mk/login.py (Caused by SSLError(SSLError("bad handshake: Error([('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')])")))
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "cmk_update_agent.py", line 1889, in main
File "cmk_update_agent.py", line 878, in run
File "cmk_update_agent.py", line 1001, in _run_mode
File "cmk_update_agent.py", line 1108, in _register_agent
File "cmk_update_agent.py", line 323, in fetch_data_from_server
File "cmk_update_agent.py", line 316, in fetch_data_from_server
File "cmk_update_agent.py", line 331, in _do_request
File "cmk_update_agent.py", line 384, in _login_site
File "site-packages/requests/sessions.py", line 578, in post
File "site-packages/requests/sessions.py", line 530, in request
File "site-packages/requests/sessions.py", line 643, in send
File "site-packages/requests/adapters.py", line 514, in send
requests.exceptions.SSLError: HTTPSConnectionPool(host='mymonitoringserver.it', port=8443): Max retries exceeded with url: /cmk/check_mk/login.py (Caused by SSLError(SSLError("bad handshake: Error([('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')])")))
2023-09-15 10:51:40,706 ERROR: HTTPSConnectionPool(host='mymonitoringserver.it', port=8443): Max retries exceeded with url: /cmk/check_mk/login.py (Caused by SSLError(SSLError("bad handshake: Error([('SSL routines', 'tls_process_server_certificate', 'certificate verify failed')])")))
Output of “cmk-update-agent register --server mymonitoringserver.it:8443 --protocol https --site cmk --hostname hostname.it --user cmkadmin --password “password” --trust-cert --verbose”:
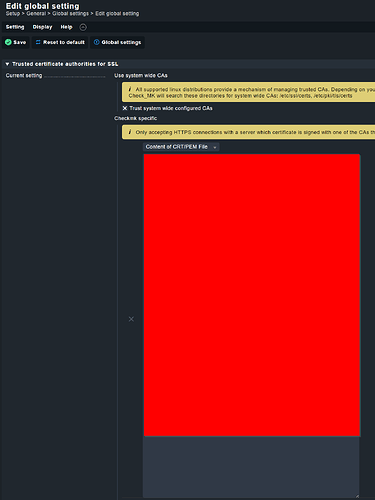
In our checkmk site we configured CA certificate in global settings:
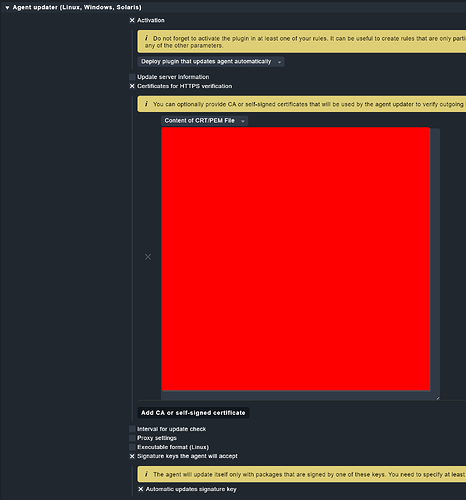
And we put the same CA certificate inside agent updater rule:
However, we always get the same error when we try to register and we see it on the Check_MK Agent service: