Hello everybody,
I think the “Fortigate Signatures” service monitoring produces some false WARN/CRIT messages in the following situation:
- on the FortiGate you can select between the standard and the extended IPS signature package at System → FortiGuard:
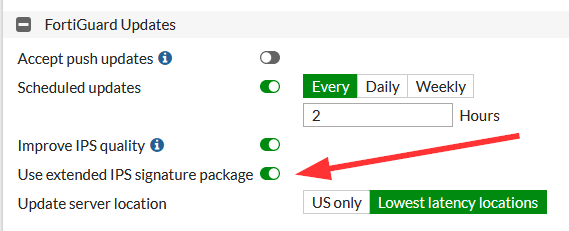
- as the screenshot shows, I am using the extended version
- verifying the current updates on the CLI of the FortiGate shows that only the “Attack Extended Definitions” are updated (have a look at the two LOOK HERE signs):
fg2 # diagnose autoupdate versions
Attack Definitions
---------
Version: 18.00177
Contract Expiry Date: Sun May 5 2024
Last Updated using scheduled update on Wed Oct 13 19:48:54 2021
Last Update Attempt: Thu Oct 14 07:52:19 2021 <<<<<---- LOOK HERE
Result: No Updates
Attack Extended Definitions
---------
Version: 18.00195
Contract Expiry Date: Sun May 5 2024
Last Updated using scheduled update on Thu Nov 11 18:49:36 2021
Last Update Attempt: Mon Nov 15 20:48:11 2021 <<<<<---- LOOK HERE
Result: No Updates
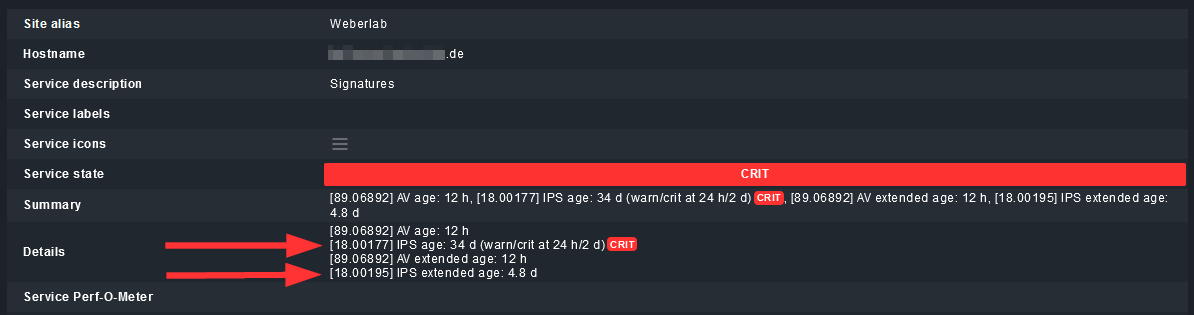
- but my checkmk plugin is complaining about the normal “IPS age”, while it shouldn’t:
I think some other posting complained about the same behaviour, but none of them pointed into that direction (?)
- [Check_mk (deutsch)] fortigate_signatures
- [Check_mk (deutsch)] fortigate_signatures
- Check-mk-fortinet-firewall-signatures-old
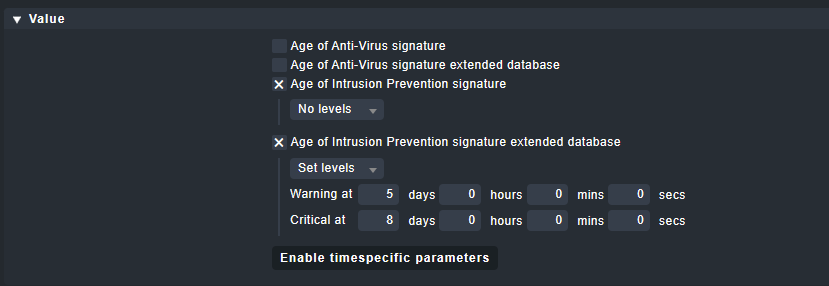
→ I think a possible solution for the plugin would be to check if ANY of those two “IPS … age” tests are up to date. I don’t think that you will ever have a situation where BOTH are up to date at the same time (unless you toggle the option at the FortiGate every other day. :))
What do you think?
Cheers
Johannes
[checkmk cre 2.0.0p12, FortiOS v6.4.7 build1911 (GA)]