I added the %s at the end of the service_name, but it complains is missing, I think is not getting it on discovery function. Because of that I want an example for try to do it.
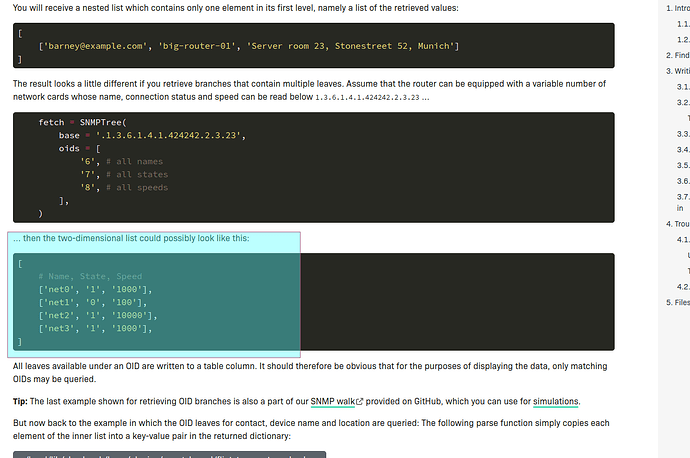
The string table I get is like this:
[[‘HUB_WAN1_0’, ‘190.24.132.38’, ‘1’], [‘HUB_LAN_0’, ‘172.20.90.66’, ‘2’], [‘HUB_WAN2_0’, ‘201.234.246.167’, ‘1’]]
Then I convert it to a dictionary with a function like this:
def parse_tunel_vpn(string_table):
print(string_table)
parsed = {}
column_names = [
"nombreTunel",
"ipTunel",
"estadoTunel",
]
for line in string_table:
parsed[line[0]] = {}
for n in range(1, len(column_names)):
parsed[line[0]][column_names[n]] = line[n]
print("Parseada la info")
print(parsed)
return parsed
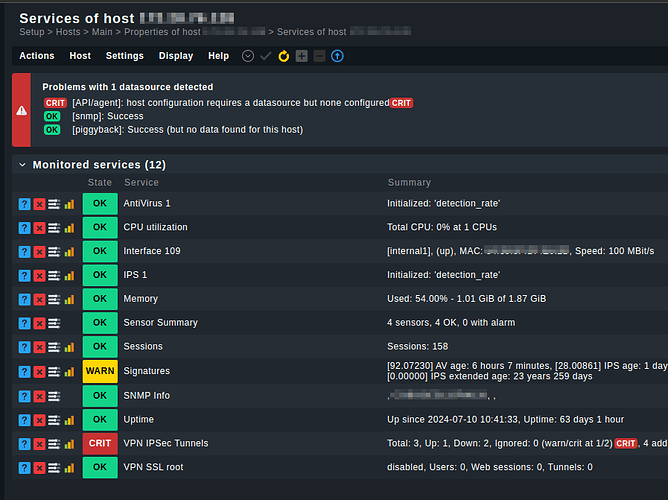
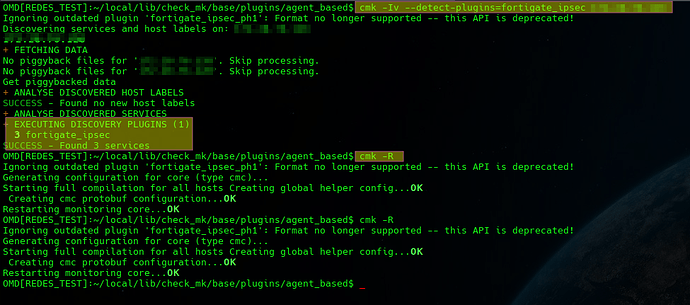
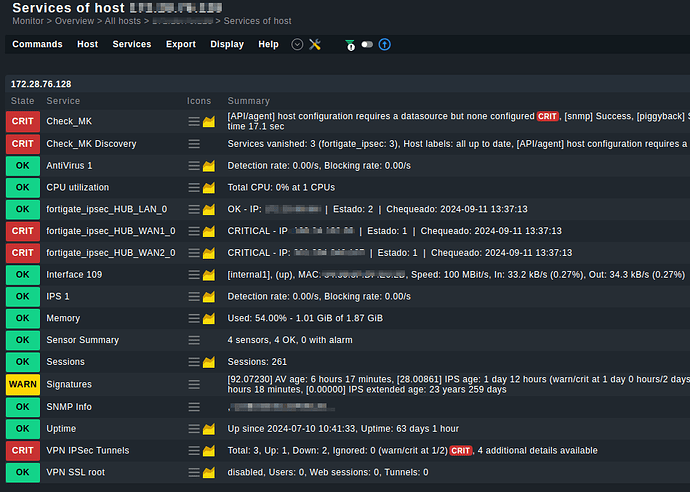
And discovery fails, it complain name is missing
Discovery method:
def discover_tunel_vpn(section):
for tunel in section:
yield Service(item=tunel)
I made so many changes in my code that sure I broke something, but I couldn’t get it work. I got the metrics from snmp without problem, but I cannot build services.
Full check code:
#!/usr/bin/env python3
# Ayuda: https://github.com/Checkmk/checkmk-docs/blob/master/examples/devel_check_plugins/check_plugin_advanced_myhostgroups.py
# + Ayuda: https://docs.checkmk.com/latest/es/devel_check_plugins_snmp.html#simulation
# Test: cmk -v --detect-plugins=tunel_vpn_setup_check 172.28.76.128
from .agent_based_api.v1 import register, Result, Service, startswith, SNMPTree, State
def parse_tunel_vpn(string_table):
print(string_table)
parsed = {}
column_names = [
"nombreTunel",
"ipTunel",
"estadoTunel",
]
for line in string_table:
parsed[line[0]] = {}
for n in range(1, len(column_names)):
parsed[line[0]][column_names[n]] = line[n]
print("Parseada la info")
print(parsed)
return parsed
def discover_tunel_vpn(section):
for tunel in section:
yield Service(item=tunel)
def check_tunel_vpn(section):
yield Result(state=State.OK, summary="Everything is fine")
register.snmp_section(
name = "tunel_vpn_base_config",
parse_function = parse_tunel_vpn,
detect = exists(".1.3.6.1.4.1.12356.101.12.2.2.1"),
fetch = SNMPTree(
base = '.1.3.6.1.4.1.12356.101.12.2.2.1',
oids = [
'2', #Nombre Tunel
'4', #IP
'20', #Estado
]
),
)
register.check_plugin(
name = "tunel_vpn_setup_check",
sections = ["tunel_vpn_base_config"],
service_name = "tunel_vpn_%s",
discovery_function = discover_tunel_vpn,
check_function = check_tunel_vpn,
)
![]()
![]()
![]()
![]()
![]()
![]()
![]()