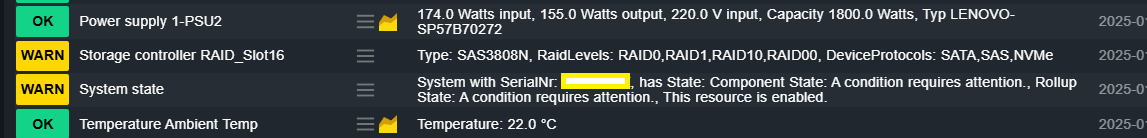
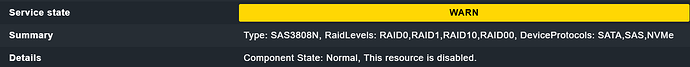
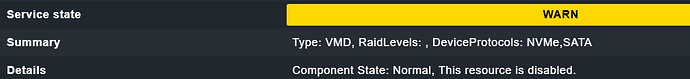
Some console tests:
# curl --insecure -v https://10.200.12.55/redfish/v1
- Trying 10.200.12.55:443…
- Connected to 10.200.12.55 (10.200.12.55) port 443 (#0)
- ALPN, offering h2
- ALPN, offering http/1.1
- CAfile: /etc/pki/tls/certs/ca-bundle.crt
- TLSv1.0 (OUT), TLS header, Certificate Status (22):
- TLSv1.3 (OUT), TLS handshake, Client hello (1):
- TLSv1.2 (IN), TLS header, Certificate Status (22):
- TLSv1.3 (IN), TLS handshake, Server hello (2):
- TLSv1.2 (OUT), TLS header, Finished (20):
- TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
- TLSv1.2 (OUT), TLS header, Certificate Status (22):
- TLSv1.3 (OUT), TLS handshake, Client hello (1):
- TLSv1.2 (IN), TLS header, Certificate Status (22):
- TLSv1.3 (IN), TLS handshake, Server hello (2):
- TLSv1.2 (IN), TLS header, Unknown (23):
- TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
- TLSv1.2 (IN), TLS header, Unknown (23):
- TLSv1.3 (IN), TLS handshake, Certificate (11):
- TLSv1.2 (IN), TLS header, Unknown (23):
- TLSv1.3 (IN), TLS handshake, CERT verify (15):
- TLSv1.2 (IN), TLS header, Unknown (23):
- TLSv1.3 (IN), TLS handshake, Finished (20):
- TLSv1.2 (OUT), TLS header, Unknown (23):
- TLSv1.3 (OUT), TLS handshake, Finished (20):
- SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384
- ALPN, server accepted to use http/1.1
- Server certificate:
- subject: C=US; ST=NC; L=RTP; O=Lenovo; CN=XCC-7D75-JZ004WWX
- start date: Jul 26 07:03:01 2024 GMT
- expire date: Jul 26 07:03:01 2027 GMT
- issuer: C=US; ST=NC; L=RTP; O=Lenovo; CN=XCC-7D75-JZ004WWX
- SSL certificate verify result: self-signed certificate (18), continuing anyway.
- TLSv1.2 (OUT), TLS header, Unknown (23):
GET /redfish/v1 HTTP/1.1
Host: 10.200.12.55
User-Agent: curl/7.76.1
Accept: /
- TLSv1.2 (IN), TLS header, Unknown (23):
- Mark bundle as not supporting multiuse
< HTTP/1.1 308 Permanent Redirect
< Date: Fri, 25 Oct 2024 20:45:11 GMT
< Content-Type: application/json
< Transfer-Encoding: chunked
< Connection: keep-alive
< Location: /redfish/v1/
< OData-Version: 4.0
< Content-Language: en
< Cache-Control: no-store
< Server: XCC Web Server
< Strict-Transport-Security: max-age=31536000; includeSubDomains
< Content-Security-Policy: default-src ‘self’; connect-src *; script-src ‘self’; img-src ‘self’ data:; style-src ‘self’; font-src ‘self’; child-src ‘self’; object-src ‘none’; frame-ancestors ‘none’
< X-XSS-Protection: 1; mode=block
< X-Content-Type-Options: nosniff
< Cache-Control: no-cache, no-store, must-revalidate, private
< X-Frame-Options: DENY
< Referrer-Policy: same-origin
< X-Permitted-Cross-Domain-Policies: value
< X-Download-Options: value
<
{“Message”:“You are being redirected to /redfish/v1/”}
- TLSv1.2 (IN), TLS header, Unknown (23):
- Connection #0 to host 10.200.12.55 left intact
cmk --debug --v
No piggyback files for ‘10.200.12.55’. Skip processing.
[cpu_tracking] Stop [7f478e4e2270 - Snapshot(process=posix.times_result(user=0.009999999999999787, system=0.0, children_user=0.0, children_system=0.0, elapsed=0.010000001639127731))]
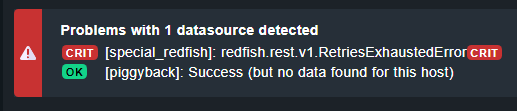
[special_redfish] redfish.rest.v1.RetriesExhaustedError(!!), [piggyback] Success (but no data found for this host), execution time 15.1 sec | execution_time=15.070 user_time=0.010 system_time=0.000 children_user_time=0.570 children_system_time=0.040 cmk_time_ds=14.450 cmk_time_agent=0.000
Agent exited with code 1: Agent failed - please submit a crash report! (Crash-ID: 9eeb3d02-9311-11ef-9299-005056801e64)
Traceback (most recent call last):
File “/omd/sites/hard2/local/lib/python3/urllib3/connectionpool.py”, line 468, in _make_request
six.raise_from(e, None)
File “”, line 3, in raise_from
File “/omd/sites/hard2/local/lib/python3/urllib3/connectionpool.py”, line 463, in _make_request
httplib_response = conn.getresponse()
^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/lib/python3.12/http/client.py”, line 1428, in getresponse
response.begin()
File “/omd/sites/hard2/lib/python3.12/http/client.py”, line 331, in begin
version, status, reason = self._read_status()
^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/lib/python3.12/http/client.py”, line 292, in _read_status
line = str(self.fp.readline(_MAXLINE + 1), “iso-8859-1”)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/lib/python3.12/socket.py”, line 707, in readinto
return self._sock.recv_into(b)
^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/lib/python3.12/ssl.py”, line 1252, in recv_into
return self.read(nbytes, buffer)
^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/lib/python3.12/ssl.py”, line 1104, in read
return self._sslobj.read(len, buffer)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
TimeoutError: The read operation timed out
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File “/omd/sites/hard2/local/lib/python3/requests/adapters.py”, line 667, in send
resp = conn.urlopen(
^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/urllib3/connectionpool.py”, line 802, in urlopen
retries = retries.increment(
^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/urllib3/util/retry.py”, line 552, in increment
raise six.reraise(type(error), error, _stacktrace)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/urllib3/packages/six.py”, line 770, in reraise
raise value
File “/omd/sites/hard2/local/lib/python3/urllib3/connectionpool.py”, line 716, in urlopen
httplib_response = self._make_request(
^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/urllib3/connectionpool.py”, line 470, in _make_request
self._raise_timeout(err=e, url=url, timeout_value=read_timeout)
File “/omd/sites/hard2/local/lib/python3/urllib3/connectionpool.py”, line 358, in _raise_timeout
raise ReadTimeoutError(
urllib3.exceptions.ReadTimeoutError: HTTPSConnectionPool(host=‘10.200.12.55’, port=443): Read timed out. (read timeout=3)
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File “/omd/sites/hard2/local/lib/python3/redfish/rest/v1.py”, line 915, in _rest_request
resp = self._session.request(method.upper(), “{}{}”.format(self.__base_url, reqpath), data=body,
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/requests/sessions.py”, line 589, in request
resp = self.send(prep, **send_kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/requests/sessions.py”, line 703, in send
r = adapter.send(request, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/requests/adapters.py”, line 713, in send
raise ReadTimeout(e, request=request)
requests.exceptions.ReadTimeout: HTTPSConnectionPool(host=‘10.200.12.55’, port=443): Read timed out. (read timeout=3)
The above exception was the direct cause of the following exception:
Traceback (most recent call last):
File “/omd/sites/hard2/lib/python3/cmk/special_agents/v0_unstable/agent_common.py”, line 149, in _special_agent_main_core
return main_fn(args)
^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/cmk_addons/plugins/redfish/special_agents/agent_redfish.py”, line 737, in agent_redfish_main
get_information(redfishobj, sections)
File “/omd/sites/hard2/local/lib/python3/cmk_addons/plugins/redfish/special_agents/agent_redfish.py”, line 577, in get_information
firmwares = fetch_data(
^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/cmk_addons/plugins/redfish/special_agents/agent_redfish.py”, line 144, in fetch_data
response_url = redfishobj.get(url, None)
^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/redfish/rest/v1.py”, line 633, in get
return self._rest_request(path, method=‘GET’, args=args,
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/redfish/rest/v1.py”, line 1118, in _rest_request
return super(HttpClient, self)._rest_request(path=path, method=method,
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/omd/sites/hard2/local/lib/python3/redfish/rest/v1.py”, line 959, in _rest_request
raise RetriesExhaustedError() from cause_exception
redfish.rest.v1.RetriesExhaustedError(!!)