Hi there,
i had a couple of times the case that we have to check the TLS Settings in Windows (Schannel) and disable unsecure protocols like TLS 1.0 or TLS 1.1.
Since there was no check for that, I’ve wrote a plugin with the help from @andreas-doehler win_firewall_status as template.
How to run:
- Deploy MKP
- Deploy the Agent Plugin via Bakery or by Hand
- You can finetune your expectations in the service rule
You can find the code and the MKP right here:
This Plugin checks for the TLS Settings (SCHANNEL) of Windows machines. To go for sure you can check and set the TLS Settings with IISCrypto → Nartac Software - IIS Crypto
Setup:
- Install the MKP
- Deploy the Plugin via Bakery
- Maybe adjust your requirements via the normal Service Rule
Assuming:
- Windows Server 2022 has enabled TLS 1.3 by default.
- Windows Server <2022 are not yet ready for TLS 1.3.
- Maybe this changes in further windows updates.
Default Warning levels:
- TLS 1.3 → Ignored
- TLS 1.2 → Client + Serverside = Enabled
- TLS 1.1 → Client + Serverside = Should be Disabled
- TLS 1.0 → Client + Serverside = Should be Disabled
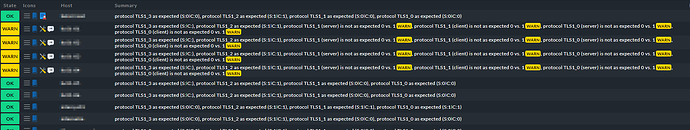
Sample Output:
- protocol TLS1_3 as expected (S:0❘C:0)
- protocol TLS1_2 as expected (S:1❘C:1)
- protocol TLS1_1 (server) is not as expected 0 vs. 1WARN
- protocol TLS1_1 (client) is not as expected 0 vs. 1WARN
- protocol TLS1_0 (server) is not as expected 0 vs. 1WARN
- protocol TLS1_0 (client) is not as expected 0 vs. 1WARN
Creds to @YogiBaer75 → GitHub - Yogibaer75/Check_MK-Things: From check plugins to website extensions I’ve used his Win_Firewall_Status as template for this plugin.
If you have some more suggestions please let me know.
Kind regards,
Constantin